Workshops
Here is a list of our 2024 workshops. Workshops are on Friday 19th July, to attend you will need a main event ticket and a (free) workshop ticket, this helps us to cap numbers as places are limited. Tickets will be released at 12 pm on the 9th of May.
Notice that some workshops are in the morning, some in the afternoon, please don’t book yourself on two morning or two/three afternoon workshop, you can’t be in two or three places at once. Pick a workshop and stick with it, you can’t wander between them. If you do book places like this, we reserve the right to cancel all your tickets without notice.
You will need your original ticket number, that came on the mail from Tito and is in the format XXXX-X. Speakers, crew, sponsors, please put your name or organisation in the box and we can validate you later.
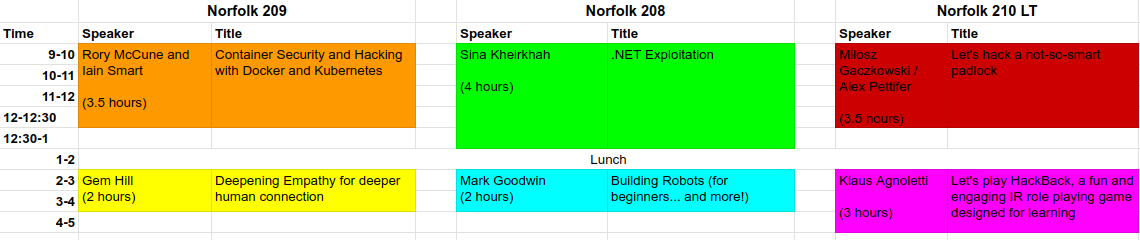
Container Security and Hacking with Docker and Kubernetes
Rory McCune and Iain Smart
3.5 hours 9 am – 12:30 pm
This hands-on workshop aims to give you an understanding of the security features and pitfalls of modern containerization tools like Docker and Kubernetes. We’ll cover a range of topics to build up a picture of the security options available and show practical examples of attack and defence on containerized systems.
There will be hands-on labs covering common attacks on Docker, Docker containers and Kubernetes clusters.
Prerequisites – Familiarity with basic Docker commands and Linux command line use will be helpful, but we’ll provide step-by-step instructions for people who are less familiar with them.
A laptop with a web browser that does not have strict filtering in place (e.g. no white-list only corporate proxies) and an SSH client will be needed for the practical labs.
Let’s hack a not-so-smart padlock
Miłosz Gaczkowski / Alex Pettifer
3.5 hours 9 am – 12:30 pm
This workshop will guide attendees through a series of common vulnerabilities in cheap Chinese smart padlocks. We will cover the process of reverse-engineering of Android applications, capturing and analysing Bluetooth Low Energy (BLE) traffic, and putting together a simple script to exploit our findings.
This workshop will be laid-back and easy to follow, intended for beginners with a working understanding of Java. We’ll bring the locks and mobile phones to control them.
Prerequisites:
- Some familiarity with Java and Python will be very helpful, but a working knowledge of another OOP language should suffice. Advanced proficiency is not required
- A laptop capable of running a standard Kali VM and able to connect to other devices via Bluetooth (we’ll bring a couple of Bluetooth adapters for those who need them)
- Familiarity with Burp Suite and Wireshark will he helpful
.net exploitation
Sina Kheirkhah (@SinSinology)
4 hours 9 am – 1 pm
.Net has always been an interesting area for exploitation, exchange, solar winds, share point, and many other critical enterprise solutions are .net based and been Pwned many times, if you like to learn how, you don’t wanna miss this.
Requirements:
- A windows 10 VM with Visual studio 2022 installed and .NET Framework 4.0 to 4.8.
- A copy of https://github.com/pwntester/ysoserial.net.
Let’s play HackBack, a fun and engaging IR role playing game designed for learning
Klaus Agnoletti
3 hours – 2 pm – 5 pm
In my workshop, I’ll dive into the world of game-based learning in cybersecurity, showcasing HackBack – a unique framework loosely based on Dungeons & Dragons that blends role-playing game elements with security training. I’ll start out explaining what HackBack is and how it works. Afterwards we’ll play a game together where we’ll play as teams and engage in passionate discussions on how to save our fictitious company from total disaster in a realistic scenario based on true events.
HackBack revolutionises traditional methods by providing immersive, risk-free simulations of security situations, both offensive and defensive, making it ideal for teaching concepts like Zero Trust and enhancing teamwork and empathy among participants. We’ll explore the open-source nature of HackBack and how it fosters a community-driven approach to cybersecurity education, making it accessible and adaptable to various settings. Join me to discover how game-based learning is a crucial, yet often overlooked tool in developing effective security professionals.
HackBack is designed for learning so it’s not necessary to know about neither Dungeons & Dragons nor Incident Response.
Building Robots (for beginners… and more!)
Mark Goodwin
2 hours – 2 pm – 4 pm
Robots look fun, right? We’d all love to build robots… but how?
This talk is about the “how”. Using some tools that most of us will be familiar with (Lego!!) and some that are perhaps less familiar… but easy (Raspberry Pi Pico) we’ll examine how to turn an off-the-shelf toy into something more special.
The session will also touch on how these tools and techniques are useful other applications (e.g. security).
Deepening Empathy for deeper human connection
Gem Hill
2 hours 2 pm – 4 pm
Empathy is an innate trait, but that doesn’t mean it can’t be practised and strengthened. In this workshop, we’ll build a picture of what empathy is, what it looks like, and how to practice it in your day to day life. Empathetic communication can help you have more meaningful and productive conversations by allowing you to build strong relationships, and build psychological safety. It will also bring greater self-awareness as you’ll learn to be empathetic to yourself, acknowledging and accepting your emotions, and seeing how they are affecting your communication.
We’ll cover how to pick up on body language, and verbal emotive language, and how to dig underneath (when appropriate) to see how these emotions are affecting conversations and decisions. Practising active listening will help us show empathy but also improve our ability to pick up on details and nuances, and learning to reflect those accurately will help gain clarification where needed.
We’ll cover active listening, reflecting and paraphrasing to show empathy, and using empathy to ask clarifying questions. We’ll also cover grounding work, to keep ourselves safe as we explore empathy with others
