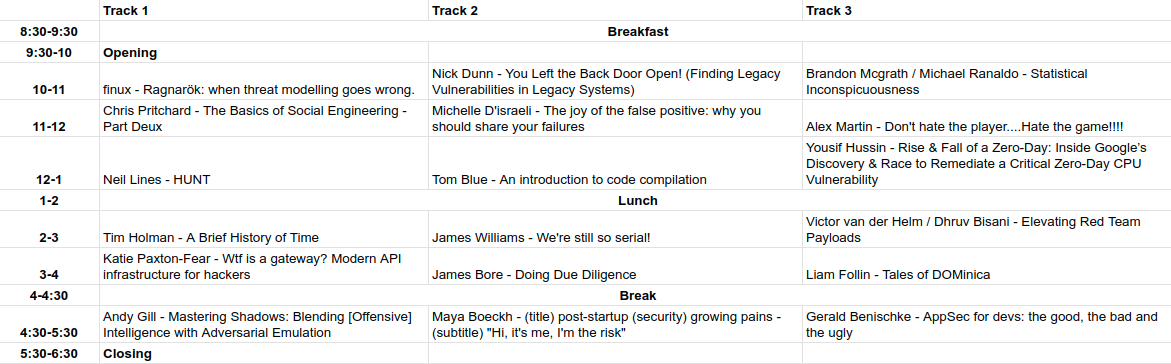
Talks
Here is the provisional talk schedule, it probably won’t change, but things happen, we will try to announce any changes when we know about them. Click the image to go to the more readable Google Sheet version.
Ragnarök: when threat modelling goes wrong (Even @ydoow would be shocked)
Finux
You’re tasked with ensuring the safety, security, and well-being of nine different locations within your organisation. Some of these locations are known to harbour hostility toward you and your organisation. Recently, you’ve received credible intelligence indicating an attack on all areas under your jurisdiction. The threat actors are specialists in asymmetric warfare, posing a significant challenge.
Your strategy? Plan thoroughly, then plan some more. Remain vigilant, continuously monitoring threat intelligence, and seize every opportunity to disrupt the adversaries’ progress. Incident response plans have been meticulously established, and key personnel have been trained and deployed, ready to defend against any threat that arises.
However, when the anticipated confrontation with the threat actors finally occurs, it unfolds exactly as feared. What if the very threat modelling meant to safeguard against such events inadvertently precipitated this outcome? Could it be that the threat is not external but internal — emanating from within?
Enter Finux, known for injecting unconventional wisdom into discussions, and this time it’s threat modelling. Brace yourself for Ragnarök—a experience likely to feature colourful language that could even leave Woody speechless. The takeaway? Perhaps it’s a realisation that hindsight is always clearer, as Finux’s unconventional approach may prompt you to reflect on your own choices: “Should I have gone to the other talk?”
HUNT (PG)
After years of red teaming, insider threats, and internal penetration testing, my focus has shifted. While I once fixated on gaining access to accounts within highly privileged groups, I’ve come to understand that the true value lies within network shares.
Armed with only an account belonging to the domain users’ group, I will reveal methods I employ during campaigns and demonstrate new tooling I have developed to assist with the hunt.
We’re still so serial! (PG)
James Williams
Unsafe Deserialization has been in the OWSAP top 10 since 2017, but did you know it can also be used for initial access and lateral movement? In this talk we will explore how .NET deserialization works, show how you can start finding your own vulnerabilities and discuss how it can be weaponized for your red team needs, with some “found in the wild” examples along the way.
Wtf is a gateway? Modern API infrastructure for hackers (PG)
Katie Paxton-Fear
STOP DOING API MANAGEMENT, APIs were never supposed to be managed, years of API development tools and NO USE FOUND for going further than JSON and REST, want to manage APIs for a laugh? We have a tool for that it’s called SWAGGER. Yes please give me AUTHORISATION, give me AUTHENTICATION, statements dreamed up by the utterly mad. LOOK at what API developers have been demanding your respect for all this time.
This talk will cover the evolving API management attack space, the tools and the techniques that developers use to deploy and manage APIs and finally how these change the security environment of these APIs.
A Brief History of Time (PG)
Tim Holman
Why the problems created by the Internet revolution 30 years ago, are still problems today. How boring old standards can actually be useful, why human beings are never proactive at work and why creating vulnerable software because you’re lazy should be illegal.
Statistical Inconspicuousness (PG)
Michael Ranaldo and Brandon McGrath
Every other week a new loader is uploaded to GitHub which is crammed full of the latest TTPs, a new tweet announces, “FUD LOADER VS CROWDSTRIKE”, and from one look a reverse engineer can identify it as a red team implant.
We spent too long playing with stats, graphs, and hundreds of thousands of malware and known goodware samples to find out why implants may stand out more than they blend in and whether there are any clear similarities and differences between them.
In this talk, we will take you through our research and compare some examples of loaders and plot them against our datasets to show you that your implant is statistically a sore thumb.
The Basics of Social Engineering – Part Deux (PG)
Chris Pritchard
You’ve seen the basics of social engineering, part one (SteelCon 2018 )
What’s the natural follow on, well part two of course! The intermediates of social engineering doesn’t quite have the same ring to it.
Joking aside, the original basics needed a follow up, and this is it.
Part two will cover:
- How to conduct physical onsite reconnaissance, and what information you’re aiming to gain from it.
- Including how to use your phone’s camera to capture things like badge design and layout, without raising suspicion.
- Taking that photo, and combining it with OSINT to then build a believable clone using a cheap badge printer.
- How to make an entrance;
- Being somewhere you likely shouldn’t be means controlling emotions, and your physical body state. I’ll talk about cloning a previous state, like how you feel when you walk into your local pub, and how to mirror that state when you walk into somewhere you shouldn’t be. Plus some details on how to act confident even if you aren’t.
- Also going to talk about emulation;
- When getting in to a building/office/casino/airport, you’re likely going to be emulating something or someone (likely as part of your pre-text story), and you’re likely to be wearing your visually cloned badge. Just how close does all this emulation need to be? Well George A Miller theorised that the brain only processes a magical number of 7 things at a time. How does this help us? I’ll explain.
- And lastly, how to deal with the success of getting inside;
- In this last section of the talk, I’ll go over how to deal with adrenaline, how to continue observing (as reconnaissance doesn’t stop once you get in), how to spot more “relaxed” areas within an office and how to use those. But also, how to achieve your objectives whether that be a place (a server room), an object (how do you find it), or a person (where are they).
Overall, a fun and engaging talk, with some war stories and real life examples from experience thrown in.
Doing Due Diligence (PG)
James Bore
Taking a real-world example where high profile infosec personalities were recruited by a fraudulent university, this talk runs through how to check if a company is not only real, but ethical and perform some basic OSINT to make sure you know what you are getting into.
We’ll cover how the fraud works, and why sometimes they may be after your credibility rather than your money.
Tales of DOMinica (15)
Liam Follin
XSS comes in three flavours, so why do we only focus on two? In this talk, we explore DOM-based XSS – the basics, how to find it, why it’s missed so often, and even some real life examples. Better yet, a series of labs have been prepared and released alongside – so you can master it as well!
Mastering Shadows: Blending [Offensive] Intelligence with Adversarial Emulation (15)
Andy Gill
Full title: Mastering Shadows: Blending Offensive Intelligence with Threat Emulation
This talk explores the combination of offensive threat intelligence with threat emulation, revealing how to map and emulate criminal tactics in targeted operations. It’s not your typical Cyber Threat Intelligence (CTI) or Red Teaming talk but a unique blend of both, offering a technical yet accessible look into the strategies of criminal organisations. I’ll also dive into the evolution of these threats and the critical role of robust operational security (OpSec) in staying ahead.
Post-startup (security) growing pains (PG)
“Hi, it’s me, I’m the risk”
Maya Boeckh
Many of us have heard the phrase “”We’re a startup, things have to go fast!””, but what happens when said startup matures a bit and slowly transitions to a small business?
I’m less interested in the journey itself, but rather the likely conclusion that everything is set to defaults, everyone is using personal devices, and everything is one unlucky event from becoming a dumpster fire.
This talk will address how, sometimes in trying to make it so one less path could lead to immediate disaster, we inadvertently break something (or everything, oops), and how to put maximum effort into not doing that whilst also maintaining focus when confronted with diverging interests.
AppSec for devs: the good, the bad and the ugly (PG)
Gerald Benischke
The relationship between developers and security professionals has not always been a harmonious one. When it works, developers come and ask questions before copy/pasting that algorithm from Stack Overflow and don’t blindly accept ChatGPTs suggestion. Security would involve themselves in the development lifecycle to enable developers. When it doesn’t work, security comes down at the last minute and tells the stupid developers that they can’t do something. And developers hate security because they’re the department of no and always push out their delivery deadlines.
This talk looks at security from a developers eyes and suggests that software development based on the agile manifesto has a lot to offer from a security perspective.
Elevating Red Team Payloads (15)
Victor van der Helm / Dhruv Bisani
Ever had your crafted Red Team payload get detected almost immediately, undoing hours of effort and forcing you to start from scratch? It’s a frustrating scenario many of us have encountered.
This presentation discusses techniques for payload development and opportunities to increase its operational lifespan, by harnessing the power of Continuous Integration and Continuous Delivery (CI/CD). We’ll explore the utilisation of GitHub Actions to streamline payload creation and using alternative compilers to our benefit. This will touch on techniques such as string obfuscation, flow manipulation and others obfuscation tricks. Lastly, we’ll also dive into opportunities for operational security (OpSec) verifications checks prior to payload release.
Join us to discover how CI/CD can assist your Red Team operations, hopefully allowing you to make faster and more resilient payloads against ever-evolving defences.
Rise & Fall of a CPU Zero-Day: Inside Google’s Discovery & Remediation of a Critical CPU Vulnerability (PG)
Yousif Hussin
Just as Vulnerability Research is an important area of focus at Google, so is Vulnerability Response to critical and complex vulnerabilities including novel discoveries affecting the CPUs. These responses not only safeguards the security of Google’s products and users but also extends its reach to millions of devices connected to the Internet, in certain instances, including the case I’m going to share here.
In this talk, I’d like to go through a recent incident at Google, including technical details, in which I was the global lead. The incident involves the discovery by a Google’s security researcher of a critical CPU vulnerability (Reptar) and the extensive remediation efforts across all of Google’s products and systems.
You Left the Back Door Open! (Finding Legacy Vulnerabilities in Legacy Systems) (PG)
Nick Dunn
AS/400 is an IBM mid-range computer series (i.e. not quite a mainframe) that’s undergone multiple name changes over the years (but still gets referred to as AS/400 by lots of people). Despite it’s age, the system is extremely stable and scalable, and still in widespread use.
This talk discusses the history of the system, and shows how the design, and computing conventions of the time have led to many of these systems existing in a vulnerable state. The talk will show how to test and exploit systems, what tooling can be used, and how to harden and protect the system. There are large numbers of these systems still in use, with many configured in a default (or almost default) state that allows easy exploitation to anyone armed with the right tools and techniques.
It demystifies a system that’s often regarded as obscure or unusual, shows what hacking techniques are needed, and best of all a lot of the hacks involve hollywood-style green text in a black terminal window.
Don’t hate the player….Hate the game!!!! (PG)
Alex Martin
Most job adverts expressly state that applicants must have a University degree, experience with a multitude of toolkits and also a minimum of 3 years of work experience.
How does someone acquire the experience needed to get their first job in the industry which will give them the experience required to get the job???
In this talk, I’ll explain how to gain experience during your time at University, how to improve your online profile, and how to appear more appealing to potential future employers.
An introduction to code compilation (PG)
Tom Blue
We’ll be delving into the process that takes place between hitting compile and getting an executable, and some of the security implications of compilation. From lexing and parsing to optimisation and code generation, we’ll cover the compilation pipeline from start to finish and explain each step, and also talk about malicious compilers and remediations for them such as diverse double compilation.
The joy of the false positive: why you should share your failures (15)
Michelle D’israeli
It is time we shared our failures, not just those rare exciting security breaches. By looking at some interesting real examples of detection events that turned out not be incidents, we will explore the value of documenting and sharing these, the useful lessons that these can still teach us, and how they can be leveraged to bring added value to an organisation beyond the security team.
This talk introduces the work of security operations teams, covering examples from supporting commercial business, finance and multiplayer video games. We explore how incidents are detected, the theory behind how we classify effects, and practical examples of how to use false positives to improve both your security endeavours and relationship with the wider business.
Most importantly, this is a fun talk about sharing things that are frustrating, so others don’t have to experience the pain too!
